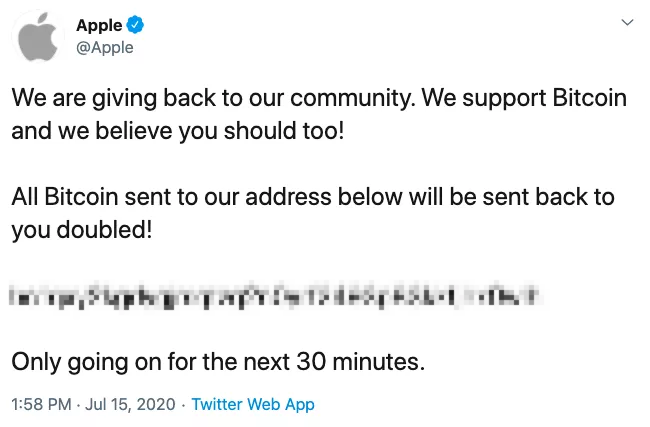
Throughout Wednesday night, multiple high-profile Twitter accounts, including those of Apple, Bill Gates, Elon Musk, Warren Buffett, Joe Biden, Kim Kardashian West and Barack Obama were compromised. The accounts were then used to post cryptocurrency scams soliciting money for a supposed payoff. Vice reported, and Twitter later confirmed, that the attack was caused by attackers gaining access to an internal tool at Twitter that let them take control of high-profile handles. One individual claiming to be behind the attack told Vice that they paid an insider at Twitter to gain access to the account. https://twitter.com/TwitterSupport/status/1283591848729219073 Such high profile accounts all getting hit at the same time was highly unusual — even accounts belonging to cryptocurrency accounts like Bitcoin's official handle were taken over to display the messages, TechCrunch reported, lending the scam more credence. A Twitter spokesperson directed us to this thread in response to our queries on how long it took the company to take action and what would be the consequences for the employees whose access was compromised to execute the hack. Twitter took over two hours to issue a statement on the compromised accounts. [caption id="attachment_218538" align="aligncenter" width="650"] An example of what compromised accounts posted.[/caption] Internal Twitter tool used for compromise "We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools," Twitter said. The company then locked all accounts that were impacted by the hack, and limited features for…